Blog Posts
When Custom Visuals started in 1995 (as Custom Data Visualizations), we were working on projects for individual companies with little emphasis on long-term projects utilizing our own servers. That all changed when an environmental company requested a web scraping application for a budget estimation project.
The project started off as a simple request to scrape a few dozen pages from a site ...
Do some industries use one type more than others?
There are a lot of terms used that describe essentially the same process of automatically getting or sending data to or from a remote site. The most common phrase is software automation, but you’ll also hear software bot, software agent, virtual robot, or just bot, all referring to the same concept. And it’s a concept Custom Visuals uses all ...
If this blog describes you or your business, please click our Contact page and let my company help out.
As you may know, Custom Visuals automates as much as we possibly can as part of our core business. We have a couple thousand unattended tasks running on our servers (co-located and in-house) on behalf of our clients throughout the day (not including the tasks the operating system runs on ...
Introduction
This series was created because we had a problem with a hacker that infiltrated our system and sent out emails in early 2015. After discussing the information with a couple colleagues and their experiences dealing with similar issues I was encouraged to share what I had created and why.
In this part of the series, I’ll provide some of the SQL code for selecting from and ...
Introduction
This series was created because we had a problem with a hacker that infiltrated our system and sent out emails in early 2015. After discussing the information with a couple colleagues and their experiences dealing with similar issues I was encouraged to share what I had created and why.
In this episode I’ll describe some of the details of the OS X Firewall and what was ...
As we saw on our previous entry of this series , we had a problem with a hacker that infiltrated our system and sent out emails.
There are three log files that are scanned for attacks, the system log, the mail log and the amavis log. They all have different formats, but they all contain the IP address of the machine contacting our server in the log line of the failed access attempt. The program ...
Early in 2015 one of the accounts on our server got hacked and was used to send out truckloads of spam emails. It took several hours for me to become aware of the issue, unfortunately. I only realized it once the number of bounces escalated to the point that our server was being blocked by other servers.
The account password was changed and some discussions were held with the user to see ...
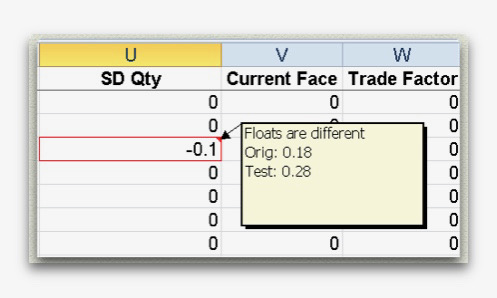
Hi all -
I gave a presentation at the Chicago Perl Mongers group on 06/25/2015 on using Perl to read and write Excel files. There is a brief discussion on the different modules for handling the 2003 and earlier .xls files, as well as the 2007 and later .xlsx files.
Writing data with different formats for headers and data, ...
As the coding geek behind Custom Visuals, I’m responsible for the application development that takes place under this roof. About half of my livelihood since 1984 has been as a small business application developer and the other half as a software engineer in larger corporations. They both have advantages ...
Welcome to Custom Visuals, LLC
This is our first blog and we wanted to welcome all of you! We thank you for your interest in our services.
Please take your time perusing our website! Feel free to ask questions, leave comments or suggestions and by all means, feel free to share this with your friends.
We invite each of you to participate on our Facebook with any weather videos ...